Threat Sharing
Threat data connect and indicators from data providers gathering in threat sharing and connect with Log (SIEM) system as well.Type of IOC

IP Address

Domain

Hash

URLs
Other
Asset Discovery
To help you find any interesting information and gathering servers and asset which service on the internet and collecting from OSINT. In the same way, we are able to import data for gap detection and threats continuously.
IP Address

Sub-Domian

Email

Discovery Tool
Data Leak Detection
Surface Web
Data leak detection from dark web that brings data of organization for publishing and selling.

Web Site

Communities

Social Network
We use indicators from insights data to detect threats from hackers stealing data or infecting Backdoor on the server.

Credential

Credit Card

Finance Info

Confidential Data

Dark Web

Threat Hunting
Threat Hunting
Threat Hunting is a system that can detect proactive threats. Also, Detection threats on cyber by using proactive indicators of insights data which come from hacker and be attacked by malware.

Persistent
Activities
System Compromised
(MITRE ATT&CK)
- File System
- Executable
- Registry
Malware Infected
(Indicator)
Compromised Detection
Compromised Detection
We use indicators from insights data to detect threats from hackers stealing data or infecting Backdoor on the server.
System
Compromised
Web Server
Compromised
Automate Update Indicator
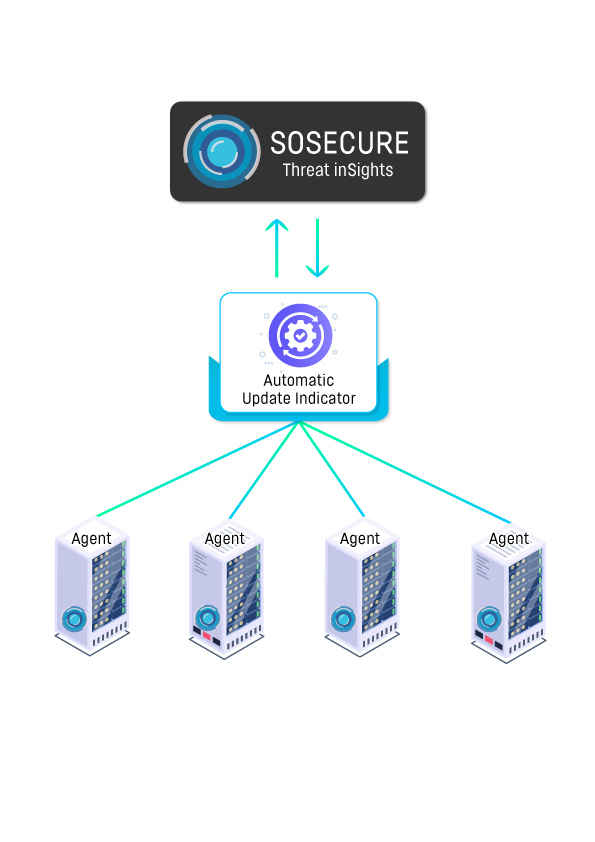
Automate Update Indicator
Threat Hunting system use indicators data and detect faster also update data for real – time

Automate
Update
Indicator
Agent-Based
Detection
Web Defaced Detection
Web Defaced Detection
เฝ้าระวังการโจมตีด้วยเทคนิคการเปลี่ยนหน้าเว็บไซต์ (Web Defaced)เพื่อรักษาความน่าเชื่อถือขององค์กร
Advanced Vulnerability Detection
Threat inSights System is able to detect the gap of the system. This system is based on a database of the Common Vulnerabilities and Exposures (CVE) system.
Passive Detection

Active Detection

Mis-Configuration Detection

Hardening and Remediation
Mis-Configuration Detection
The system can detect unsafe configurations based on Security Guideline from the CIS center.Also, editing configuration for safety from the system.

Detection user attack by using social engineering technique such as Phishing, Fake mobile application, Drive-By-Download.

Phishing

Fake Mobile
Application
Drive-By
Download
Social Engineering Detection

Cybersecurity News Feed
Update news about cybersecurity from other sources around the world and getting notifications via Email.
Contact Us
410/ 34 Soi Ratchadaphisek 24, Ratchadaphisek Rd, Samsen Nok, Huai Khwang, Bangkok 10310
Support@sosecure.co.th
061 564 5294
@sosecure